AI-powered scams blur lines, mimicking trusted voices and creating sophisticated traps....
O365 monthly license fees are increasing. See how this impacts your budget....
Is This the Ultimate Access Point? We recently tried out the Ubiquiti UAP-AC-PRO, and it has proven to be a solid choice for anyone looking to enhance their wireless network. This access point reached...
The Ultimate VPN Router for Business Needs? If you’re looking for a reliable router that handles multiple connections with ease, we recently tried out the DrayTek Vigor 2866. This device stands ...
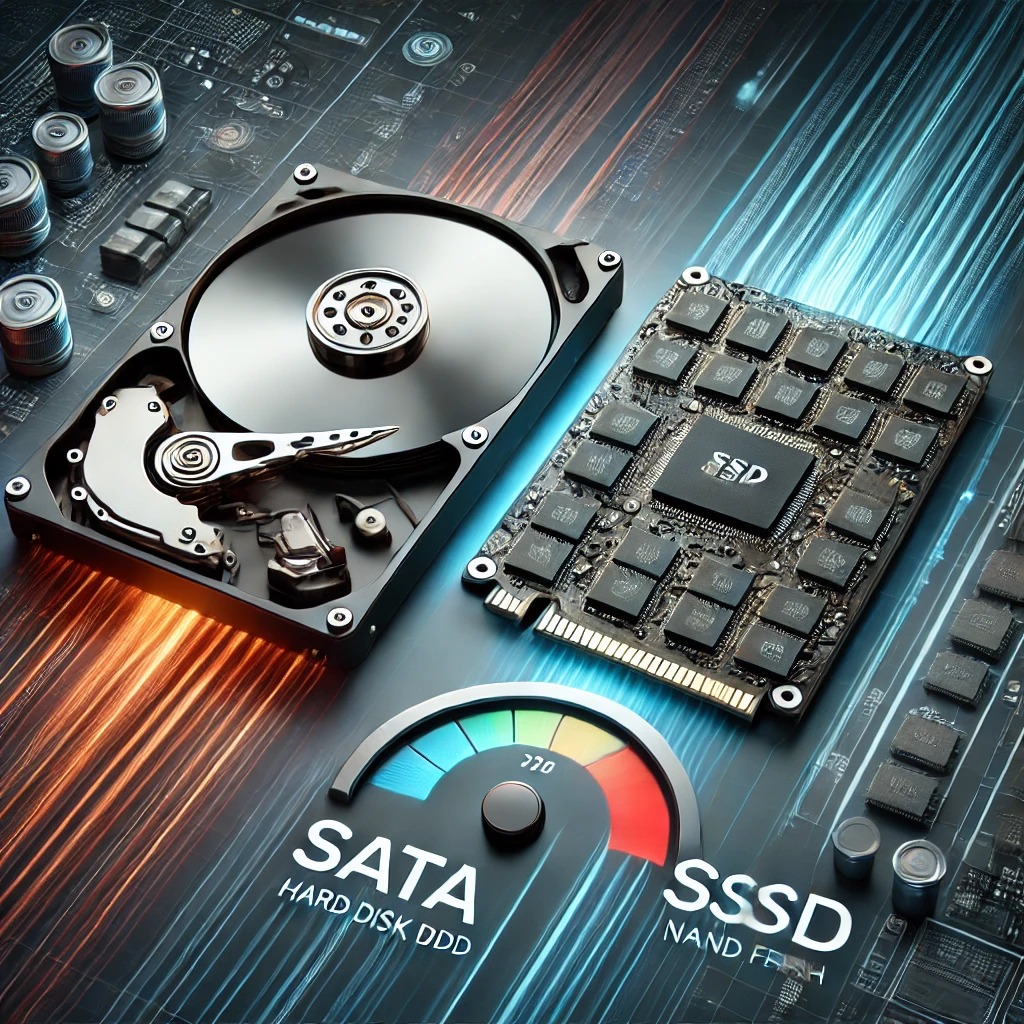
Understanding the Key Differences in Storage Technology When comparing SATA vs SSD, it is essential to understand their key differences. SATA drives are generally slower and use older technology, whil...
Which is Best for Your Internet Needs? Wifi vs Wired Connection, When it comes to internet connectivity people often choose between Wi-Fi and wired connections. Wired connections are generally faster ...
AI-Powered Threat Detection and the digital realm, while offering unparalleled opportunities, presents a constantly evolving threat landscape. Cyberattacks are becoming increasingly sophisticated, oft...
Multi-factor authentication (MFA) is essential for protecting sensitive information in an online world where cyber threats are constant. Using MFA significantly enhances security by requiring addition...
A Beginner’s Guide to Understanding Artificial Intelligence Artificial Intelligence (AI) is a rapidly evolving field of technology that seeks to create machines capable of performing tasks that ...