VOXI Mobile Review, I’ve been using VOXI Mobile for over two years now, and it’s one of those services I simply haven’t had to think about — which, in mobile terms, is a very g...
Surfshark vs NordVPN are often compared because they target a similar audience: users who want a VPN that is fast, reliable, and easy to use. However, their approach to pricing, device limits, and eve...
Private Internet Access vs NordVPN are both well-established VPN providers, but they are designed for very different audiences. Where NordVPN focuses on ease of use and feature-rich applications, Priv...
IVPN vs NordVPN are both respected VPN providers, but they represent very different approaches to trust, transparency, and company ethics. Where NordVPN focuses on scale, performance, and mainstream u...
Mullvad vs NordVPN represent two very different philosophies in the VPN space. Both provide strong encryption and protect users from routine online tracking, but they are designed for different types ...
Proton VPN vs NordVPN are two of the most recognisable VPN services available today. Both offer strong security, modern apps, and global coverage. However, they are built with very different prioritie...
NordVPN Alternatives, NordVPN is one of the most recognisable VPN brands in the world. It is fast, widely supported, and packed with features. For many users, it works perfectly well. However, popular...
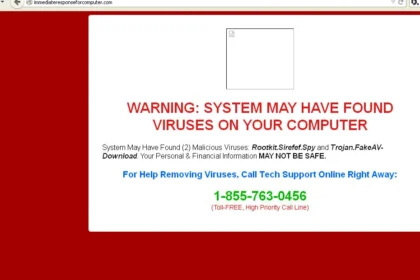
Best Free Antivirus – Start HereIf you’re searching for the best free antivirus, you’re not alone. After dealing with pop-ups, viruses, or ransomware, most home users want protection...
Flipper Zero FAQs, This FAQ answers the most common, realistic questions people ask about the Flipper Zero in 2026. These are based on actual user concerns, misunderstandings, and expectations—b...