Your Best Defense Against Ransomware, Ransomware attacks are becoming more common and can cause serious harm to any business. Regularly backing up data is the best way to protect a company from the ef...
Employee training plays a crucial role in protecting organisations from cyber threats. Many people think that only technical staff can defend against these risks, but the truth is that non-technical s...
Many people do not realise how important it is to keep software Updates updated. Outdated software can create serious risks for users, making them vulnerable to cyber attacks. Regular updates are cruc...
Small businesses often think they are too small to be targeted by cybercriminals. In reality, a security breach can have a devastating impact on their operations and reputation. Implementing simple cy...
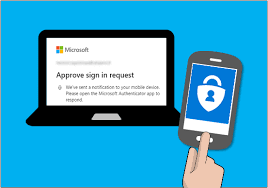
Many people may think their passwords are enough to keep their accounts safe. However, cyber threats are more sophisticated than ever, making passwords alone insufficient. Adding Multi Factor Authenti...
Evaluating the Flaws in Recent Age Restriction Legislation...
Social engineering is a tactic used by cybercriminals to exploit human vulnerabilities. These criminals manipulate individuals into providing sensitive information, such as passwords or bank details. ...
Infrastructure Advances When the dust settles, will you be proud of how far you’ve come, or haunted by the chances you didn’t take? Why todays infrastructure advances matter in an era defi...
Overview A critical vulnerability, CVE-2025-49763, has been identified in Apache Traffic Server (ATS) versions 9.0.0–9.2.10 and 10.0.0–10.0.5, affecting the Edge Side Includes (ESI) plugin...